Your Guide to the Creation of HIPAA-Compliant Software
Table of contents
What makes a healthcare tech product successful? Ingredients include well-thought-out functionality, quality of services your organization offers, reliable partnerships, investments in development, and compliance to industry standards, including HIPAA.
HIPAA compliance is the key to increase trust to your business, meet customer expectations, and provide extra protection to vulnerable data healthcare organizations are dealing with. And in this article, we are going to guide you through all the essentials related to HIPAA-compliant software development, answering the questions: What is HIPAA? How to become HIPAA-compliant? What are the must-have features of HIPAA-compliant software? What are the things to consider before and after the software implementation?
What is HIPAA?

So what’s the information that needs to be protected by HIPAA? It consists of personal identifiers that can lead to the disclosure of personal information. These could be phone numbers or social security numbers, fingerprints or voiceprints, health insurance beneficiary numbers or medical record numbers, photos or geographical identifies, etc. All these identifiers, in one or in combination, can lead to the disclosure of medical history, or, say, payment information on an individual, which can cause them (and, for sure, the organization where data leak happened) serious problems.
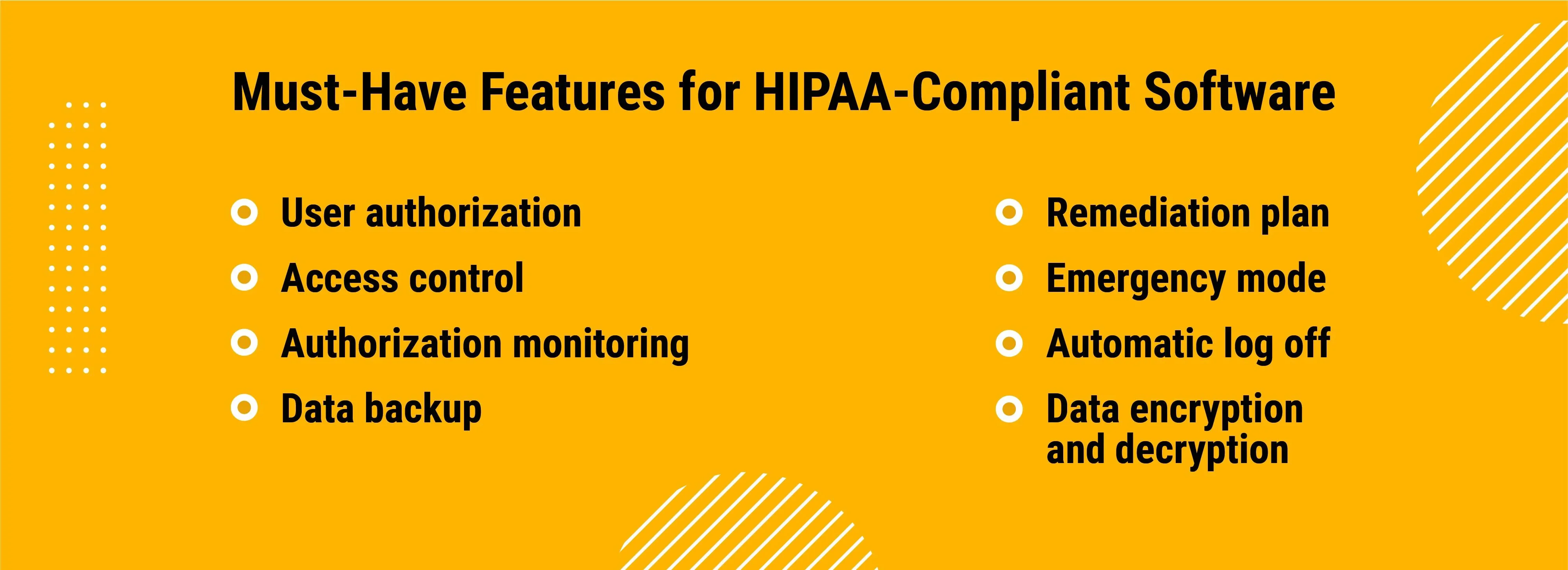
HIPAA-Compliant Features the Medical Software Must Have
And what are the necessary features of software that offer extra protection to patient sensitive data? The list below contains those that derive from the HIPAA Security Rule.
But things are not as simple as just the provision of the list of features. There are recommendations developers need to follow to meet the requirements set by HIPAA standard.
How to Be HIPAA-Compliant?
Here are the essential elements that make software under development HIPAA-compliant.
Regular Audits
As it is defined in the Act, regular audits need to be conducted to eliminate the possibility of data breaches or privacy violations. After the audit, it’s required to provide detailed information on risks and errors if there are any.
Recovery Plan
Audits and their results play an important role in the creation of a recovery plan that would initiate in case of a threatening situation.
Data Storage
Violation of HIPAA regulations can cost companies up to $1 million, and that’s why one of the crucial steps to take is to ensure reliable data storage. It has to protect organizations from the risks of hacker attacks and ensure ePHI (electronic protected health information) security.
Relationships with Business Associates
The software should also be capable of handling organization’s relationships with contractors responsible for ePHI management.
Security
Software also has to detect any breaches, and if there are any, automatically create a corresponding report. After that, preliminary measures have to be applied to avoid further data leaks.
Things to Consider When Implementing HIPAA-Compliant Software
Although features and steps described above do matter, HIPAA software should not be considered by organizations as a panacea. To be effective and to drive the desired outcomes, it has to be implemented in a well-prepared environment. And here are things that can ensure its successful implementation and operation.
Physical Security Policies
A physical security policy defines people having access to equipment used within your company and those allowed to enter certain facilities. For example, a policy can include a list of your employees who can enter server rooms or laboratories, or use medical safes. Also, the policy should describe the way it must be enforced: for example, in relation to guests entering your premises.
Access Control
Access control policies should describe in detail how people with access should use programs and equipment. Because you deal with sensitive data, it is required to establish a must-follow step-by-step guide, which will contain information about the right way to submit a request for access, the followed-up procedure of approval or rejection of the submitted requests, the frequency of account audits, record-keeping, etc.
Workstation Use Policies
It specifies safeguards on using and accessing systems. For example, it can contain information about the number of attempts a user can take to access the system, provides recommendations on the strength of passwords and how users should keep them (for example, restricting them from writing passwords down on paper and sharing with other employees).
Security Awareness
This includes security training provided for newcomers to the company, annual/monthly pieces of training for all hires, timely delivery of information about security policy updates to employees, reminders, etc.
Malicious Software
In addition to using some antivirus software, a company must also have a written protocol on the frequency of updates to virus definition, ways to respond to a virus outbreak, reporting about potential risks, etc.
Disaster Recovery
While all the measures described above are aimed at reducing the possibility of disasters, there are still cases when something can go wrong (a server goes down, there's a prolonged power outage, etc.). And that's why a company should have established disaster recovery policies and procedures that ensure the possibility of data backup and recovery, allow to identify emergencies, and offer plans on how to respond to them.
Remember, you are no less responsible for the safety of data than your software development provider.
HIPAA-Compliant App Development: Concluding
Now you know what HIPAA-compliant software and what it takes to create it. Still, we have some pieces of advice for you to conclude this short guide:
- Because the failure to follow HIPAA rules correctly can cause serious consequences, we at Emerline recommend starting the design of healthcare systems with HIPAA requirements in mind.
- For sure, there are cases when a company changes its course but wants to go further with the same solution, that now needs to be HIPAA-compliant. For such cases, we recommend security tests that allow companies to ensure that the existing solution has no critical vulnerabilities.
- What’s more, companies that want to ensure continuous security, maintained compliance, agility, and enhanced performance to their healthcare systems can take advantage of our vast DevOps expertise.
So wherever you are — in the process of medical app idea creation and validation or with the existing solution at hand that needs expert support, enhancement, rebuild — our teams have got you covered! Feel free to contact us at any time, with any questions.
Published on Jul 27, 2021





